
Autonomy in the industrial and commercial transportation (ICT) industry is racing forward. After all, semi-autonomous and autonomous construction, mining and agriculture vehicles are advantageous, offering benefits in terms of safety, efficiency and sustainability, which can have a positive effect on the bottom line.
As it stands today, vehicles in the mining and construction industries are already leveraging some degree of automation to drive throughput and increase worker safety on the job. Manually operated and autonomous vehicles use sensor-guided systems to make tight turns in constrained spaces, turn in unison to avoid collision and avoid rolling over. Even with partial autonomy, vehicle and worker safety and productivity improve when using these systems.
From a productivity standpoint, autonomous vehicles can operate for longer periods of time and do not require rest breaks or shift changes. Routes are also able to be optimized, leading to less wear and tear on the vehicles themselves.
In terms of sustainability, the increased efficiency and fuel economy delivered from semi-autonomous vehicles also delivers value by helping to reduce fuel consumption, which can decrease costs while positively impacting the environment.
 Figure 1: Off-highway vehicles are becoming more autonomous and interconnected thanks to the rise of electrification, which makes them more vulnerable to cyber attacks.TE Connectivity
Figure 1: Off-highway vehicles are becoming more autonomous and interconnected thanks to the rise of electrification, which makes them more vulnerable to cyber attacks.TE Connectivity
Intersection of Autonomy and Cybersecurity
These types of semi-autonomous/autonomous vehicles, as well as drones and other robotic machines, are transforming the off-highway sector, and we can expect to see these devices used even more in the coming years as more realize their benefits. In fact, the global autonomous off-road equipment and machinery market is estimated to experience a compound annual growth rate (CAGR) of almost 13% between now and 2032.
While this growth is impressive, it is not without its challenges. The automated safety features built into today’s off-road equipment are controlled by software. Whenever software is involved, cyber vulnerabilities become a major concern.
On a jobsite, a cyberattack could result in a takeover of equipment and a disruption of projects. What’s more, construction and mining sites require real-time communication between systems, workers and vehicles. If this is compromised, safety could be jeopardized and accidents could happen. When it comes to farming, a breach could mean crops are destroyed, resulting in operations being impeded and lost revenue.
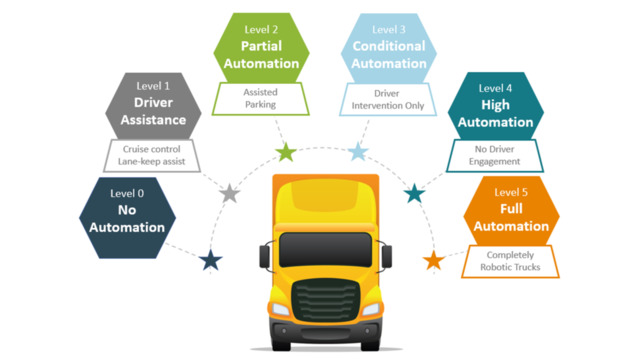 Figure 2: How autonomous a vehicle is ranges from no automation whatsoever to being driven completely by robots. Each comes with benefits and risks.TE Connectivity
Figure 2: How autonomous a vehicle is ranges from no automation whatsoever to being driven completely by robots. Each comes with benefits and risks.TE Connectivity
Electronification Intensifies Cybersecurity Needs
Autonomous functionality isn’t the only example of the exponential increase in the reliance trucks and off-highway equipment have on software and data. Commercial equipment is now incorporating sensors that gather data from other vehicles and even the environment itself using cameras and LiDAR and connecting to cloud-based platforms to enable advanced navigation and fleet management services.
For example, on a jobsite, GPS systems with LiDAR and RADAR sensors integrate with telematics software to provide the real-time location of all machinery, while proximity and other sensors detect blind spots and the proximity of nearby equipment, information that can then be used to improve safety, productivity and performance.
Remote condition monitoring and diagnostics also are becoming more common in the industry with information on the vehicle’s status or equipment being used to prevent maintenance issues before they occur.
The result of all this new technology is the creation of massive amounts of data. And as this data becomes more interconnected and intertwined, the more vulnerable it becomes as well. If an attacker were able to access and manipulate vehicle data, incorrect decisions could be made, operations could be impacted, or injuries could occur.
For example, an operator controlling a backhoe at a construction site can avoid hitting a utility line thanks to a cloud connected device that limits how deep the equipment can dig. If a hacker were to take control of the data or manipulate it in some way, the operator might act in error, putting themselves, bystanders, their equipment and the project at risk.
Four Ways to Minimize Cyber Threats
While the threat of a cyberattack could stall work at a jobsite is real, there are ways to minimize those risks and ensure the systems are as secure as possible with these four methods:
- Decide what data to collect and store. Off-highway vehicles are using more and more sensors to collect data on system performance and conditions. This data is typically captured and streamed into large data lakes to enable real-time analytics. However, these cloud-based systems can have potential gaps and vulnerabilities. As a result, designers should carefully consider the data they are collecting and how long that data may be available to the end user.
- Assess vehicle-to-everything (V2X) communications. Heavy equipment, such as construction or mining vehicles used in tight operating environments, need V2X communications to adapt their response to changing conditions, especially when they need to coordinate movement and turns. These vehicles should have robust encryption protocols to protect all V2X traffic. However, slower-moving equipment, such as tractors used on farms, may be able to use less robust cellular networks if they don’t need to communicate with other vehicles or maneuver around them.
- Determine what’s wireless and what’s not. While using wireless sensors and antennas to capture and transmit all data is tempting, it creates greater risks. Original equipment manufacturers (OEMs) may consider saying wired for internal communications and using shielded copper cables and connectors for external communications.
- Leverage advanced technology to improve security. Data analytics can uncover security gaps and vulnerabilities so teams can address them before they impact vehicle operations. Data integrity solutions can validate the authenticity of data transmitted from sensors and systems. AI-based systems also can detect behavioral anomalies, such as unusual driving patterns, while adaptive security protocols can automate a corrective response, such as cutting vehicle power.
Innovation and Vehicle Security Go Hand in Hand
Vehicle security and minimizing cyber threats need to be top of mind for OEMs as the commercial vehicle industry continues to add new features and functionality through electronification and autonomy.
By joining forces with component manufacturers, connectivity providers and security system vendors, OEMs can evolve security strategies, systems and processes. This is important in the off-highway sector because many companies rely on third-party vendors for autonomous technology. All in all, as the industry continues to progress forward, OEMs and end users can rest assured vehicles are secure, resilient and adaptive thanks to their collective efforts.



















